Optimizing the design, function, and benefits of the logical cyber-representation of physical asset environments, whether for wells being drilled or produced, pipelines, or treatment facilities, is an evolving trend for the oil and gas industry to gain operational efficiency. The analysis described shows that operational efficiency and cybersecurity compromise is essential for business success when constructing the information and control models.
Cybersecuirty is crucial for every function within the oil and gas supply chain. It is important to pay attention to the data flow to protect the data and facilities, while developing capabilities to deal with intrusions. This is the essence of cybersecurity and operational leadership.
This article emphasizes the value gained by investing in cybersecurity for upstream operations—including drilling, workovers, and completions—whether the operations are capital-, technology-, or personnel-intensive, and remote and extended infrastructures must be included.
The most effective strategy for ensuring the cybersecurity of industrial control systems is the iterative process because threats are constantly changing and security has an experience curve.
Successful cybersecurity requires a careful consideration of various business aspects. And it depends on an integrated approach to addressing science and technology, economics and business, government and regulations, and society and social behavior. Importantly, security is never just about an information technology problem but is rather a core business issue.
Corporate cultures that have laid out clear responsibilities for employees at different levels have fewer security gaps because every employee is aware of his or her area of responsibility in managing risk. The risk matrix is a useful tool for assigning responsibilities. It will also boost the company’s defense base against hacks. Another key tool for integrated physical and cybersecurity systems is a safety-instrumented system (SIS).
Oil and gas companies with successful security are those that reach out across the community to address the likelihood of risks and to prioritize the exchange of knowledge.
Multiple engineering and research programs have addressed cybersecurity for downstream operations of the oil and gas industry (SPE 162304, 106687, and 149015). Other projects have discussed remote upstream operation information and logic models that have been implemented to digitize the upstream industry, moving it to a new level of automation, efficiency, and improved overall performance.
The perks of the transforming digitization include assurance, cross-organizational collaboration, leveraging of knowledge, and safer operations with minimal human presence on the wellsite as a result of remote control (SPE Economics & Management and SPE 174779).
On the other hand, when adding intelligence, you add sensors, controls, and networks. This digital expansion creates vulnerability and more entry points—back doors—to exploit defects and weaknesses. One of the reasons for this proliferation of weaknesses is that no logical system can perfectly describe a physical system because there are too many pieces. For instance, it is difficult to represent people’s behavior or to model the interface between human and machine (SPE 165918).
The value of the data and information that is gathered represents a security risk for upstream operations. In the fields of exploration and drilling, geophysicists, geologists, and petroleum engineers use big data to make valuable predictions and test underlying assumptions (sensitivity analysis) before making business-critical decisions. Geophysicists increasingly use large masses of data and rely on faster computing and processing technologies to build seismic maps and subsurface images.
Similarly, geologists use data to form theories about the downhole subsurface structure and how it was formed over millions of years. They survey the area looking for patterns or anomalies that would lead to a potential resource discovery.
During development drilling and completion activities, information security is useful for validating data to prevent human error and optimize environmental management, for example by preventing a well blowout by using accurate pore pressure data obtained through measurement-while-drilling systems. A gap in data may affect operational performance (Fig. 1). On the other side, quality data availability helps in simulation, and yields close estimates of downhole profiles and aims to reduce operational risks.
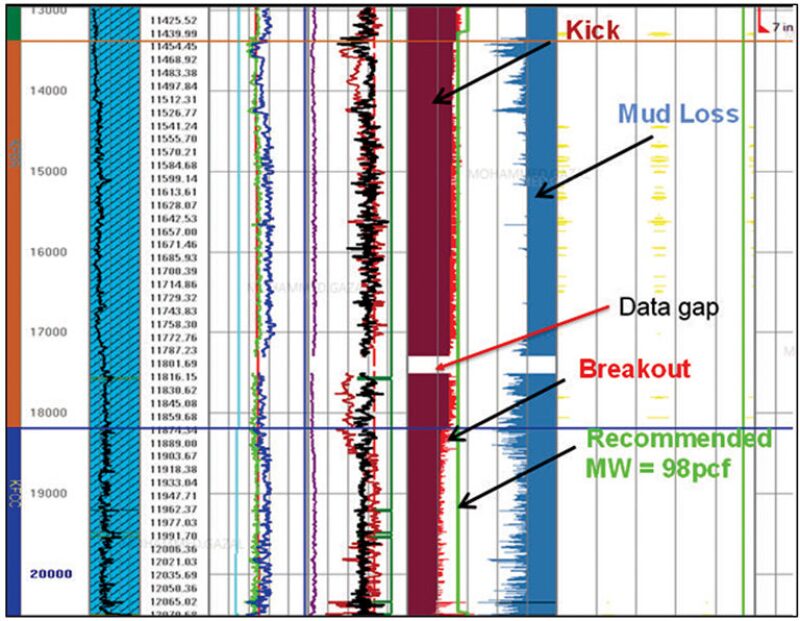
The Unintended Threat
There are three major reasons for the vulnerability of oil and gas infrastructure and facilities. First, upstream oil and gas represents the world’s largest supply chain, involving numerous subcontractors who supply equipment, fluid, and other services to run operations. Second, the function of oil and gas companies is connected to the economy and society where they operate. Third, threats and security defenses are constantly evolving and changing, while facilities may change slowly at best. This makes cybersecurity of such long-lived assets very complex, especially because decisions taken will last a long time and cost a lot.
Additionally, the extended reach of today’s oil and gas infrastructures into remote operational areas creates vulnerability and security exposures as well as environmental risk. Accidents in such extended facilities result in liability increases, revenue loss, and loss of safety standing with society and authorities.
While there has been substantial emphasis for decades on physical security in production plants and on drilling rigs, cybersecurity is still evolving and building an experience curve as threats grow. Table 1 compares the nature of cyberthreats to that of physical threats.

Experience has shown that an iterative security strategy is effective in detecting, mitigating, and preventing cyberthreats because those threats are constantly changing. The iterative strategy, as defined by the Center for Chemical Process Safety of the American Institute of Chemical Engineers, strives to enhance secure operations by
- Eliminating hazards completely.
- Reducing the likelihood or severity of a hazard by means of equipment, operation, or process redesign.
- Substituting a less hazardous material or using a less hazardous process to reduce the potential or consequences of human error, equipment failure, or intentional harm.
In addition, the iterative approach accounts for the entire lifecycle of a system, including the associated hazards and risks and economic feasibility. Table 2 shows how the orders of the iterative approach can be scaled to cybersecurity (Center for Chemical Process Safety 2010).

Integrated Cyber- and Physical Protection Systems
Cyber- and physical security are concerned with the management of unintended events. Because of the complexity of the energy business, it is best to look at the solution through the lenses of a system. This complexity stems from the multiple interacting parts of the energy system, producing behaviors that would not be necessarily expected, including reactions to things imposed on it from the outside that were not originally anticipated.
The system approach helps to create a more accurate understanding of the cause and effect pattern, enabling analysts to better predict outcomes and deal with surprise. The main components of this security system span science and technology, economics and business, government and regulations, and society and behavior.
One of the key aspects in understanding security is to recognize that the logical system does not perfectly represent the physical system and to knowing where the resulting weaknesses will appear. Network security consists of activities and policies to safeguard timely access to services, the integrity of data flow, and the levels of trust between systems and users.
OSIsoft, a company that offers information management and data acquisition support for major industrial infrastructures around the world, has proposed a defense system with three threat interaction categories: visibility, access, and trust (VAT). VAT guides the formulation of defensive actions and neutralizes how a threat interacts with assets.
Regarding visibility, targets should not be visible and advisories should be highly visible. Looking at access, it is essential to reduce access to the absolute minimum level needed to achieve system deliverables. In the realm of trust, it is best to spread trust among multiple administrators rather than directing it toward a single point of potential failure in your architecture.
All secure deployment zone architecture patterns revolve around these three categories. It is critical to select the appropriate deployment architecture. Adopting the wrong architecture can lead to problems stemming from potential two-way communication, which creates pathways for bad actors to access the system (Owen 2013).
An SIS handles critical safety functions by bringing a process to an equilibrium condition when breaches from acceptable operating limits take place. A successful example is the Linking Oil and Gas Industry to Improve Cybersecurity (LOGIIC) model, which is a collaborative public- and private-sector effort to protect oil and gas infrastructure.
SIS are targeted by LOGIIC to protect control networks. An SIS harmonizes logic control data with relevant security data at different network architecture levels that are function-specific to offer safety functions, while controlling existing and emerging cybersecurity breaches. The ongoing, function-specific assessment and development for SIS is promoting inherently safe logic models with resilient safety controls (Tudor 2011).
Information Risk Management
The risk management exercise is a useful tool to understand the problem context, identify risks and causes, assess potential consequences, and evaluate treatment strategies that will eliminate and reduce hazards. It also suggests how to communicate lessons learned for improvement opportunities.
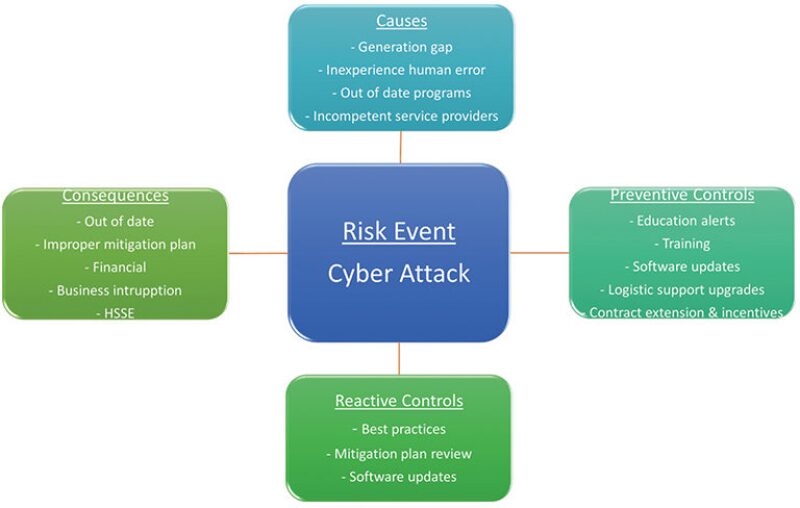
Fig. 2 represents the steps of risk management as applied to a general cyberattack scenario. The simulated scenario involves cyberattack risks originating in one of two ways.
- Social engineering phishing with web-based delivery that corrupts the user’s hard drive and causes it to lose all of its information.
- Phishing with web-based delivery that lets hackers enter the user’s computer system, where they can see all personnel/secured/sensitive materials and use that to harm the user or the company.
The risk matrix will close gaps and assign responsibilities that will increase the difficulty of a cyberbreach, increase detection capability, and abate negative consequences.
Conclusions and Recommendations
- Industrial data flow and control logic models are the digital brains that monitor, manage, and control the vast interconnected networks of upstream operations.
- Experience has shown that an iterative security strategy is effective in the detection, mitigation, and prevention of cyberthreats because those threats are constantly changing.
- SIS allow for technical integration of data without compromising the safety functions.
- The ongoing, function-specific assessment and development for SIS is promoting inherently safe logic models with resilient safety controls.
- Company cultures that have clear responsibilities for employees at different levels experience fewer security gaps; every employee is aware of his or her area of responsibility in managing the risk. The risk matrix is a useful tool in assigning responsibilities. This will also boost the company’s defense base against hacks.
- It is also essential to recognize that when making a cybersecurity recommendation, it is not possible to compute the outcome perfectly because of uncertainty. But it is possible to influence the direction of the outcome in ways that will reduce the likely negative impact of future events.
Acknowledgments
The authors would like to thank the management of Saudi Aramco for its support and permission to publish this article. Also, part of this article is derived from the cybersecurity course offered by the University of Southern California. The authors acknowledge the support of Professor Donald L. Paul.
References
SPE 106687-MS Information Architecture Strategy for the Digital Oil Field by B. Burda et al.
SPE Economics & Management. The Implementation of a Drilling-and-Completions Advanced Collaborative Environment—Taking Advantage of Change by S.J. Sawaryn et al.
SPE 149015-MS Protection of Petroleum Industry From Hackers by Monitoring and Controlling SCADA System by A. Vijay and V.S. Unni.
SPE 162304-MS Protecting the Digital Oil Field from Engineering Cyber Threats by A. Al-Issa.
SPE 165918-MS Ensuring Data Security for Drilling Automation and Remote Drilling Operations by C.J. Cavazos.
SPE 174779-MS Implementation of Drilling Systems Automation—Halifax Workshop Summary: Industry Standards, Business Models, and Next Steps by F. Florence et al.
Center for Chemical Process Safety, The American Institute of Chemical Engineers. 2010. Final Report: Definition for Inherently Safer Technology in Production, Transportation, Storage, and Use.
Owen, B. 2013. Recommended Deployment Patterns, talk presented at OSIsoft Users Conference, San Francisco 16–19 April.
Tudor, Z. 2011. Cyber Security Implications of SIS Integration With Control Networks, talk presented at Automation Week, International Society of Automation, Mobile, Alabama USA 17–20 October.

