Fool me once, shame on you; fool me twice, shame on me. That’s an adage that often alerts us to the dangers of knowing—and yet not mitigating—the repercussions of risk. And with the resurgence of cyberattacks globally, it’s also a wakeup call to cyber readiness.
The oil and gas industry faces particular risk—though it’s not necessarily ready (Fig. 1).
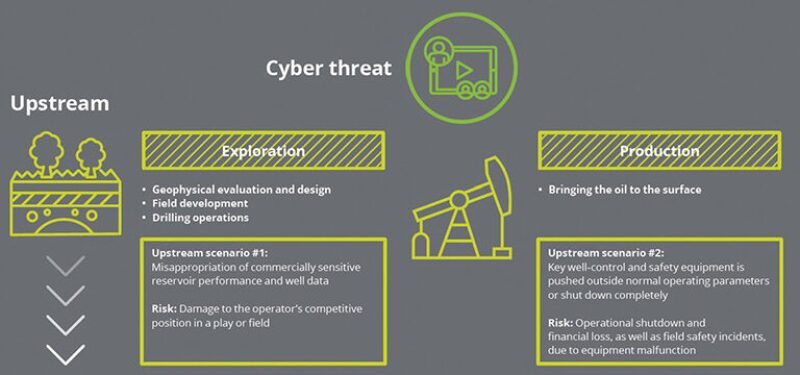
Sixty-one percent of oil and gas professionals who are responsible for cyber risk said their organization fell short last year in protecting and securing its industrial control systems (ICS). Sixty-eight percent surveyed said their organization had experienced at least one cyber compromise in the past year, resulting in OT disruption or the loss of confidential information (Ponemon 2017).
And perhaps most alarming: They did not have a clear strategy to address it.
This is an industry where the opportunities for infiltration are nearly limitless. A typical large oil and gas company uses half a million processors just for reservoir simulation; it generates, transmits, and stores petabytes (each equal to 1,015 bytes) of sensitive field data; and it operates thousands of drilling and production control systems in diverse locations, with numerous fields, vendors, service providers, and partners (Mittal et al. 2015).
ICS are used to control assets spanning thousands of square miles—such as the 2.6 million miles of oil and gas pipeline in the US alone (PHMSA). ICS may be as simple as a few panel-mounted controllers or as complex as interconnected and interactive distributed control systems with thousands of field connections. At the same time, cloud-based internet of things (IoT) technology, wireless communications networks, and analytical and automated tools are connecting operations in real time, with new data-based links between rigs, refineries, and headquarters.
And as these connections multiply exponentially, the exposure—and thus the threats—increase.
“The industry is increasingly becoming a target, with attacks growing in frequency, sophistication, and impact. Data is becoming more valuable, perhaps the most valuable commodity in the world right now, and oil and gas companies are oozing with data,” Ben Dickinson, global cybersecurity lead for ABB’s oil, gas, and chemicals unit, said at the 2019 SPE Offshore Europe conference.
The Quandary of Connectivity
Operational technology (OT) systems such as wellsite sensors and programmable logic controllers (PLCs) are intended to perform tasks with nonstop availability. On the other hand, information technology (IT) systems such as enterprise resource planning place a priority on security over availability. The conflict comes when stringent IT security measures introduce latency into time-critical control systems and potentially compromise availability and operational response.
“Despite the many benefits of modernizing enterprise technologies and IT/OT convergence, networking of production systems, machinery, and equipment is progressing faster than their security measures. The convergence of OT and IT, with their often-conflicting priorities, is increasingly exposing companies to a new realm of risk,” according to IKARUS Security Software.
Leaving a Legacy of Liability
At one time, the risks were lower due to the physical separation of systems and decentralization of security at a unit level. ICS were traditionally standalone systems used for automation and data acquisition. Globally, about 1,350 oil and gas fields have been producing for more than 25 years, using systems and equipment from different vintages throughout that period (IT Data Solutions 2019).
Much of this equipment was designed decades ago without security features, and there was no concerted effort to mitigate online threats. One of the biggest problems in oil and gas security, particularly in IoT, is the age of the technology. “If it’s working, it doesn’t get replaced. They’re not going to necessarily go back and update remote sensing locations,” said James M.T. Morrison, distinguished technologist in cybersecurity with Hewlett Packard Enterprise.
A 2018 Oil & Gas IQ report said, “… despite an increase in investment, the oil and gas sector is suffering a shortfall in cybersecurity confidence and capability. One of the major reasons why the industry finds itself in this state is its recent foray into technologies associated with the internet of things and the general move toward increased connectivity.”
OT assets operating in the field were often engineered before the widespread digitization of ICS. While oil and gas companies are benefiting from going digital, that step change has significantly stepped up cyber risks. Fifty-nine percent of respondents to the 2017 Ponemon study believed there is a greater risk in the OT than the IT environment. Sixty-seven percent believed their ICS are at substantially greater risk because of cyber threats.
The Cyber Security for the Oil and Gas Sector (COGS) project, a collaborative of the Department of Homeland Security, agrees that the security of all systems is jeopardized as legacy components are integrated with networked systems and made more accessible.
This is often seen when large companies acquire small or midsize oil and gas companies, and they are still running Microsoft DOS on some machines, or Windows XP which is no longer supported. Those new connections expose refineries, pipelines, and offshore oil platforms to online threats.
To ensure security, legacy systems often must be reworked, modified, or retrofitted. The problem is that upgrading scores of devices could cost millions, and companies often find it too expensive and time-consuming to patch software running high-dollar facilities and processes. Even a 4-hour security upgrade can stop production for days.
That’s because little redundancy is built into OT networks—for example, should a system lose a front-end controller, there is not another one to take its place. If there is no redundancy, changes cannot be made unless the system is taken offline.
But the reality is, security typically loses out to operations. “If I have to take a sensor offline to perform an upgrade, the business decision is typically ‘no, we’re not taking it offline,’ ” Morrison said. Necessary software updates and security patches are often not made.
Thus, supposedly safe systems open the backdoor for espionage and sabotage.
Consequences of Contamination
In any industry, companies face the prospect of contamination of data in the form of ransomware, data breaches, and intellectual property theft. These risks are magnified in the oil and gas industry due to the political and economic impact of disruptions and highly volatile processes.
Trend Micro, a security firm, attempted to lure attackers to a dozen fake ICS—referred to as “honeypots”—in 2016. Within a few months, hackers from 16 different countries found the systems on public search engines. Seventy percent of the attackers even penetrated the systems and extracted data. About 15% of the attacks could have caused the ICS to shut down.
Whether hackers use spyware targeting bidding data for fields under consideration, malware infecting production control systems, or a denial-of-service attack that blocks the flow of information through control systems, they are becoming increasingly sophisticated and coordinated in their attacks.
More than a third of the attacks on critical infrastructure were untraceable or had an unknown “infection vector” (Mittal et al. 2015). That’s why cyber breaches can remain undetected for days.
When a company evaluates its risk of cyberattack, it is important to assess how an attacker might manipulate sensors, actuators, or processes to impact the physical environment, and then put in place redundant controls in the ICS.
“Ransomware is the crime du’jour on the internet right now, but so far OT networks are unaffected,” Morrison said.
But once hackers make the jump to the OT network of a midsize operator in a midstream system, and deny the company access to OT sensor data in an offshore or remote oil platform, that could change the game. At that point, the criminal mindset is all about how to develop a money stream.
“Once they get control of a pipeline segment—and prove they have control, maybe by causing a certain valve to close—they have a limited amount of time before the company sends someone to fix the valve. They know they need to move quickly to collect their ransom,” Morrison said.
Companies then would face the difficult prospect of paying to get that data back. “Off the record, oil companies are saying of course they’d pay,” he said. “And scary as it sounds, we could potentially see this happen in 3–5 years.”
Once that does happen, the number of attacks will escalate, and all bets are off.

An OT Network Is an OT Network
In June, Honda motors got hit and the company shut down production at its car assembly line in at least three countries. According to Morrison, if Honda shut down production, that means the hackers jumped the gap and entered the OT network. And regardless whether the industry is oil and gas or car manufacturing or healthcare, he said, an OT network is an OT network. If an infiltrator was able to access an OT network, it’s very easy to leverage that attack in another industry.
Or in another country.
If a criminal wanted a concession from a country, and he knew it is somewhat dependent on oil and gas production, could he hold the system hostage on a threat to damage that production?
If an attacker finds a vulnerability in a front-end controller that’s being used in one industry, he or she likely will wonder who else—in other industries or countries—is vulnerable to this attack. That’s the kind of question a criminal would ask—and from a defense standpoint, oil and gas companies need to ask the same questions and make sure those vulnerabilities don’t extend to their domain.
Unfortunately, the bad actors make a practice of sharing their insidious methods. Once hackers figure out a means to access—and monetize that access to—the OT network, co-conspirators will learn how it’s done and leverage it for their own desires, either by sharing or selling their code.
These days, hackers don’t have to buy ransomware or even know how to code it. They can have someone else code it for them. If one is able to produce ransomware that can cause damage to an OT network, it’s a good bet the code will be shared and monetized quickly.
More Complicating Factors
In addition to undertaking the challenge of untangling, policing, and securing a web of IT and OT systems, companies must consider two other factors: an absence of oversight and the presence of human error.
Lack of standards and regulations. Although strict cybersecurity regulations govern power, chemical, and nuclear facilities, oil and gas companies are not regulated by federal standards for cybersecurity.
Industry leaders have tried to develop their own best practices and standards, but no single set has been universally agreed upon and adopted—so the sector sometimes lags behind other industries in their response to digital threats.
The companies are not required to report instances of hacking, so we have an incomplete picture of the number of attacks and the effectiveness of a company’s controls. Homeland Security publishes data on cyberattacks, but with no reporting requirements, those data represent only a small share of the attacks against the energy industry.
“Let’s say a company I do business with got hacked. Only 15% of the time will they report what happened at the risk of reputational damage,” Morrison said.
Human Error. While sophisticated cyberattacks may be launched to steal trade secrets and boost foreign industries and economies, systems can also be compromised—and damaged or disabled—not by malicious intent but by human error.
The top cybersecurity threats are negligent or careless employees, said 65% of Ponemon respondents; only 15% of those surveyed cited insiders with malicious or criminal intent (2017).
“Insider threat is always listed as the number-one threat. These are your colleagues and friends,” said Tom Winston, Cyber Security Engineering professor at George Mason University. “But the reality is, that’s not the case.”
The biggest threat to an ICS may be workers who are not malicious but rather careless or clueless.
In one petrochemical example cited by Morrison, two companies were sharing a data center where there were a number of switches, and an employee mistakenly plugged into the other company’s switch, causing a great deal of confusion and consternation when the company detected other traffic appearing on their network.
In other non-malicious—albeit negligent—practices, individuals are often the ones who create exposure, a chink in the armor of otherwise secure systems. Among their errors, operators might make incorrect configurations, PLC programming errors, or forget to monitor key metrics or alerts.
The Risk Is Real
Nearly 900 cybersecurity vulnerabilities were found in US energy control systems between 2011 and 2015—more than in any other industry—with threats of infrastructure sabotage, insiders, ransomware, and malware, according to Homeland Security’s ICS Computer Emergency Response Team.
As recently as April, across all industries there were 623 advisories for 91 unique vendors in 406 products and 512 unique versions. This is nearly a 40% increase in advisories compared to March and the number is steadily increasing month over month: there has been a 67% increase since February 2020. (Ozkaya 2020).
The C-level decision makers are feeling the pinch. KPMG found that oil and gas chief executives ranked cybersecurity as the largest threat to their organizations’ growth. More than half of the CEOs in the sector believed that their organization would at some point fall victim to a cyberattack.
Cybersecurity firm Dragos agrees that the first cyber-related ICS event to cause major process and equipment destruction or loss of life will occur in the oil and gas sector—across any of the three major stages of operations: downstream, midstream, or upstream, particularly in the area of exploration and production.
“We’re going to need really smart humans who know this problem, understand that we’re going against human threats, and ask how we can go above regulations to reduce risks to our companies,” Dragos CEO Robert Lee said. “That always hasn’t been the topic.”
Supplier Beware
A company’s supply chain is exposed to insidious attacks by hackers who study every connection for possible weaknesses. Sixty-nine percent of Ponemon respondents believed their organization was at risk due to the uncertainty of security practices throughout their supply chain. Sixty-one percent said their organization was having difficulty mitigating those risks.
Since there are limited controllers for oil and gas OT networks, if a hacker can infect the software update for front-end controllers, and he knows which companies use that manufacturer’s controllers, how secure is that software supply chain? The attacker could potentially enter the downloader and insert a remote access tool—as one did in spreading the Energetic Bear virus over a 3-year period starting in 2011.
Energetic Bear, dubbed “the new reality of cyberwarfare” by Symantec, infected the ICS of hundreds of European and US energy companies when attackers infiltrated three ICS manufacturers and then inserted the malware in legitimate software updates sent to clients.
The three-phased campaign—consisting of phishing emails, watering-hole attacks, and Trojanizing of legitimate software bundles—followed in the footsteps of Stuxnet in 2010, the first known major malware campaign to target an ICS.
References
Bean, G., Mittal, A., and Slaughter, A. Connected Barrels: Transforming Oil and Gas Strategies with the Internet of Things. Deloitte University Press. 2015 (accessed May 2020).
Bronk, C., Lee, R., and Winston, T. Baker Institute. Bits, Barrels, and Bad Actors: Cyber Threats to the Oil and Gas Industry webcast. 26 June 2020. https://youtu.be/iXAzbmgOfL4
Ikarus Security Software. IoT, IIoT, ICS: Definitions, Similarities and Differences. 24 September 2019 (accessed May 2020).
Ozkaya, E. Monthly Vulnerability Review. June 2020 (accessed June 2020).
Ponemon, L. Ninth Annual Cost of Cybercrime Study 2019 (accessed May 2019).
Ponemon, L. The State of Cybersecurity in the Oil & Gas Industry: United States. February 2017 (accessed May 2020).
Slaughter, A. and Zonneveld, P. An Integrated Approach to Combat Cyber Risk: Securing Industrial Operations in Oil and Gas. Deloitte. 2017 (accessed May 2020).
US Department of Homeland Security. Cyber Security for the Oil and Gas Sector (accessed May 2020).
US Department of Transportation Pipeline and Hazardous Materials Safety Administration. PHMSA FAQs (accessed May 2020).
More on JPT Online
With evolving targets and techniques, the digital landscape is quaking. Are you cyber-ready for the threats? Read more at http://go.spe.org/Is_Oil_Gas_Invincible_to_Cyberattack.


